Overview
OWASP Noir is an open-source project, specializing in identifying attack surfaces for enhanced whitebox security testing and security pipeline.
What is noir?
Noir is an open-source project dedicated to identifying attack surfaces, enhancing whitebox security testing, and optimizing security pipelines. It excels at discovering API endpoints, web endpoints, and other potential entry points within source code for comprehensive security analysis.
This tool was developed using Crystal. Initially started as hahwul’s personal project1 in August 2023, it became an OWASP project2 in June 2024, co-led by hahwul and ksg.
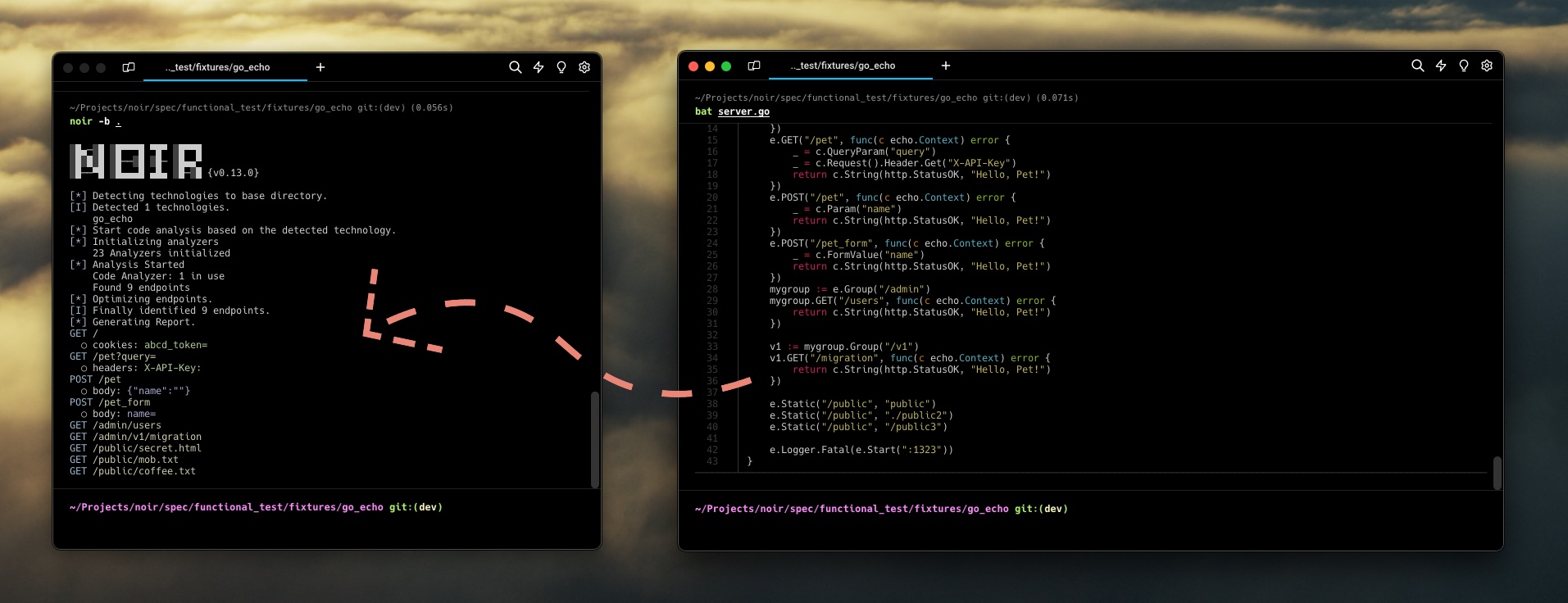
How it works?
Noir is composed of several key components: detector, analyzer, deliver, minilexer/miniparser3, output-builder, and passive-scan & tagger4. These components interact and work together to effectively analyze source code. Through this process, they help identify endpoints, parameters, headers, and more within the source code.
flowchart LR
SourceCode:::highlight --> Detectors
subgraph Detectors
direction LR
Detector1 & Detector2 & Detector3 --> |Condition| PassiveScan
end
PassiveScan --> |Results| OutputBuilder
Detectors --> |Techs| Analyzers
subgraph Analyzers
direction LR
CodeAnalyzers & FileAnalyzer & LLMAnalyzer
CodeAnalyzers --> |Condition| Minilexer
CodeAnalyzers --> |Condition| Miniparser
end
Analyzers --> |Condition| Deliver
Analyzers --> |Condition| Tagger
Deliver --> 3rdParty
Tagger --> |Tags| OutputBuilder
Analyzers --> |Endpoints| OutputBuilder
OutputBuilder --> Report:::highlight
classDef highlight fill:#f9f,stroke:#333,stroke-width:4px;
Road Map
We plan to expand the range of supported programming languages and frameworks, and to continuously increase accuracy. Furthermore, we will leverage AI and Large Language Models (LLMs) to significantly broaden our analysis capabilities.
Initially conceived as a tool to assist with WhiteBox testing, our immediate goal remains to extract and provide endpoints from the source code within the DevSecOps Pipeline. This enables Dynamic Application Security Testing (DAST) tools to conduct more accurate and stable scans.
Looking ahead, our ambition is for our tool to evolve into a crucial bridge, seamlessly connecting source code with DAST and other security testing tools, thereby facilitating a more integrated and effective security posture.
About the project
License
OWASP Noir is distributed by an MIT license.
Contributing
Open-source projects thrive on the strength of the community. From small contributions to major ones, we want to express our gratitude to all contributors. If you’re interested in contributing, please check out this document.
We believe every contribution counts and appreciate the time and effort you put into making this project better. Whether you’re fixing a typo, adding a new feature, or improving documentation, your help is invaluable. Thank you for being part of our community!
To get started, simply follow the guidelines in the Contribute Guide. It’s full of helpful tips and instructions to make your first contribution smooth and enjoyable.
Happy contributing!
Thank you to the contributors of Noir ♥️
PassiveScan Rule contributors
Code of Conduct
OWASP Noir is committed to fostering a welcoming community.
View our Code of Conduct on our GitHub repository.
Help and feedback
We always welcome feedback. Please share your thoughts, suggestions, or report any issues via the GitHub discussions or issues page.